Secure Hash Algorithm 256
Hash?
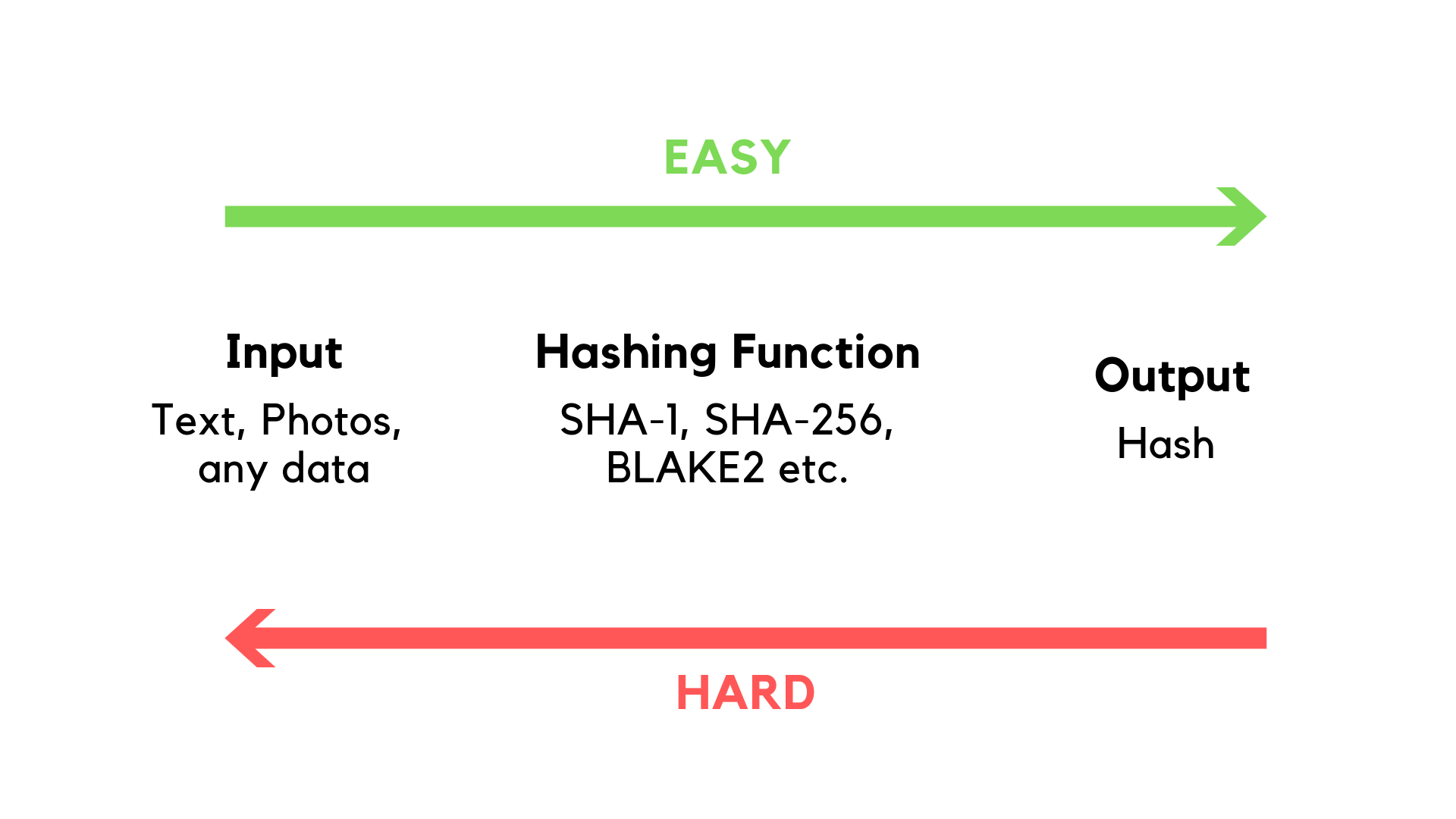
Where did I hear that? You may ask yourself these questions when you look upon the title. Well cryptocurrency has been over the headlines on the news and other media for the past two years or more depending where you are from. Well SHA is just an algorithm that is the bedrock of the block chain and by extension cryptocurrency. SHA is what is called a deterministic one way hashing algorithm. Upon dissection that definition yields a clear picture of what SHA is; deterministic means that the algorithm will yield a specific output for a given input, it is also referred to as one way since there is no algorithmic way to do the function backwards at least not yet and it is a mathematical function that takes any size input but has an output of a fixed size hence the hash in the nomenclature.
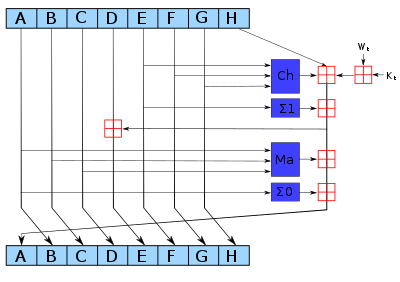
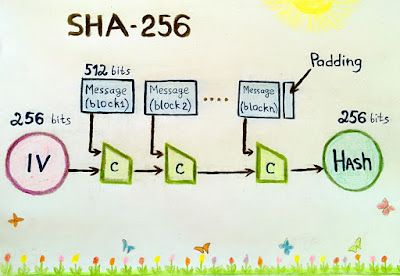
Where did I hear that? You may ask yourself these questions when you look upon the title. Well cryptocurrency has been over the headlines on the news and other media for the past two years or more depending where you are from. Well SHA is just an algorithm that is the bedrock of the block chain and by extension cryptocurrency. SHA is what is called a deterministic one way hashing algorithm. Upon dissection that definition yields a clear picture of what SHA is; deterministic means that the algorithm will yield a specific output for a given input, it is also referred to as one way since there is no algorithmic way to do the function backwards at least not yet and it is a mathematical function that takes any size input but has an output of a fixed size hence the hash in the nomenclature. The only way that seems to work is brute force and that is not an algorithmic approach. So now that we know what SHA is, what does it do? SHA 256 is an algorithm that produces a 256 bit long identifier for any length of digital media. So let us say you have a petabyte of video files in an archive and wanted to assign a digital finger print to that archive, running the file through the SHA 256 algorithm will produce a unique, non-reproducible identifier for that file that is only 256 bits long usually expressed in 64 hex digits; the only way to reproduce that identifier (finger print) would be to have an exact copy of that archive. The algorithm is also ingenious in the sense that it is developed with the butterfly effect in mind, ie. a slight change in a digital file which has a SHA 256 identifier will yield a drastically different SHA 256 identifier. I am talking about the slightest of changes like changing the rgb values of a single pixel on a digital photograph by a factor of 1. So how many different hashes or digital finger prints are there? Well that is simple math lol, just 2 to the power of 256.
115792089237316195423570985008687907853269984665640564039457584007913129639936 hashes or one hundred and fifteen quattuorvigintillion seven hundred and ninety two tresvigintillion eighty nine duovigintillion two hundred and thirty seven unvigintillion three hundred and sixteen vigintillion one hundred and ninety five novemdecillion four hundred and twenty three octodecillion five hundred and seventy septendecillion nine hundred and eighty five sexdecillion eight quindecillion six hundred and eighty seven quattuordecillion nine hundred and seven tredecillion eight hundred and fifty three duodecillion two hundred and sixty nine undecillion nine hundred and eighty four decillion six hundred and sixty five nonillion six hundred and forty octillion five hundred and sixty four septillion thirty nine sextillion four hundred and fifty seven quintillion five hundred and eighty four quadrillion seven trillion nine hundred and thirteen billion one hundred and twenty nine million six hundred and thirty nine thousand nine hundred and thirty six.
Calling this an astronomically large number would be an insult to the number. For reference, the diameter of the observable universe is 93 billion lightyears, ie one hundred septillion. Calling SHA 256 the world’s most computed algorithm would be an understatement and the algorithm is the basis for cryptography, authentication, digital signatures etc. No one and I mean no one has figured out a way to reverse the algorithm. The bitcoin protocol currently operates on SHA 256 and the algorithm was developed by the NSA (National Security Agency). So, I am sure you remember the cryptocurrency mining craze that was ongoing for the better part of 2018 and into 2019 that drove the prices of graphics cards flying. Well, what does mining bitcoin really mean? Well the ledger for bitcoin as most of you will know is known as the block chain and as the name suggests it is a chain of blocks (set of records) that are joined using cryptography. Mining in a sense is record keeping, ie. keeping the blockchain unalterable, consistent and complete. Each block has the SHA 256 hash of the previous block and that links it to the previous block; miners will have to use brute force tactics to generate the SHA 256 hash of the previous block or a close enough match. By doing so they will have generated bitcoin, hence the name mining. I will cover the block chain and the details of how the bitcoin protocol operates in a future review. Takes this as an introduction to the algorithm that underlies blockchain.
This is Kerod from Yaltopya Tech
signing off.